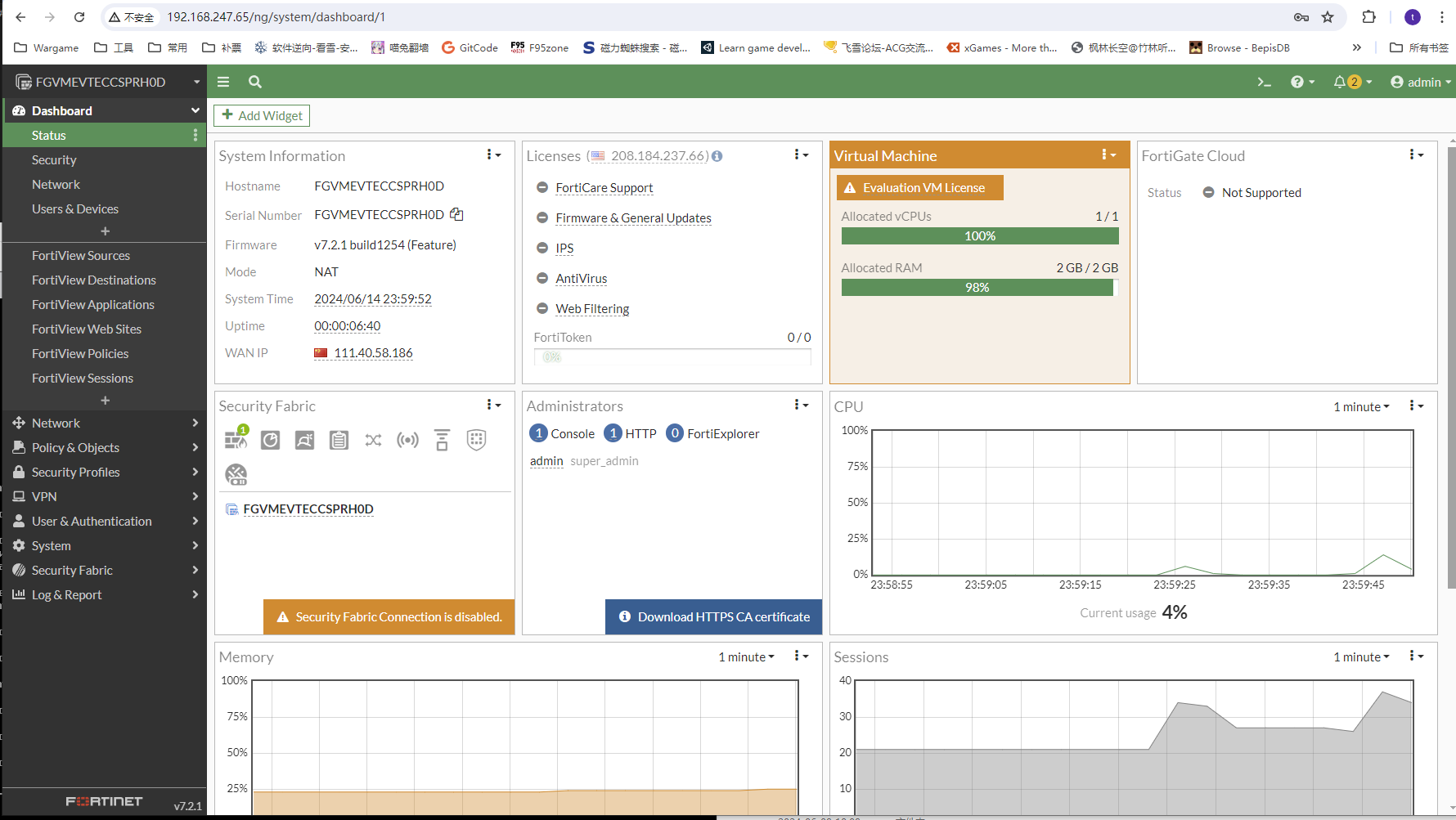
参考一些网络上的教程配置fortigatef路由器
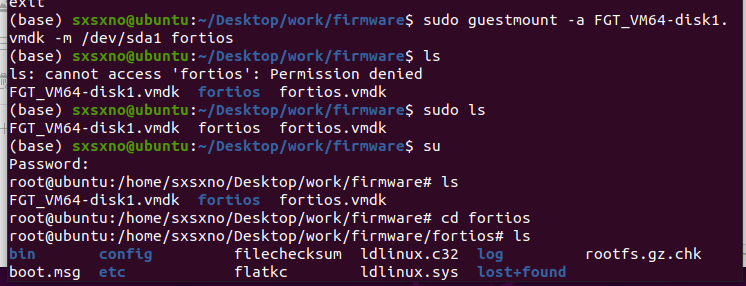
1 | sudo virt-filesystems -a fortios.vmdk 查看磁盘分区 |
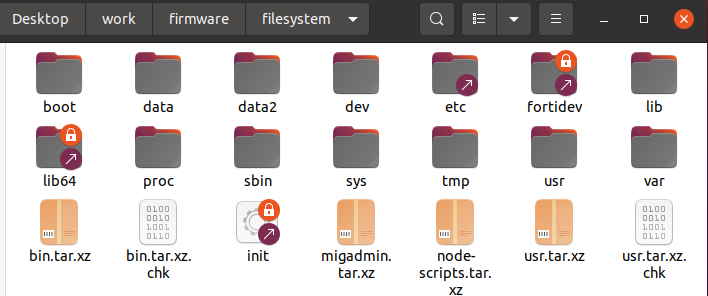
复制一份rootfs.gz,解压出来
1 | sudo chroot . /sbin/xz --check=sha256 -d /bin.tar.xz |
题目内容:parse the payload
样本估计是bvp47
https://www.pangulab.cn/files/The_Bvp47_a_top-tier_backdoor_of_us_nsa_equation_group.zh-cn.pdf
根据下面这篇文章解出payload
https://www.qianxin.com/news/detail?news_id=6484
解payload的exp
1 | import re |